memory_lane
Points : 537
Solves: 19
My team NULLKrypt3rs is the 4th pwner of this question. In this question we have a vmem(Virtual Memory) file which is a memory dump of a system. I first think of that this file may be analyse with volatility framework and we have to extract the secret folder from their, this may be the intended solution for this question, i wasted approx 2 hrs with analysing file with volatility framework with no result at last. So, i think why i can’t use other way to extract files and then i use foremost to extract the file.
$ foremost Memory_lane.vmem -o test/ And i found some folders which contains bunch of files.
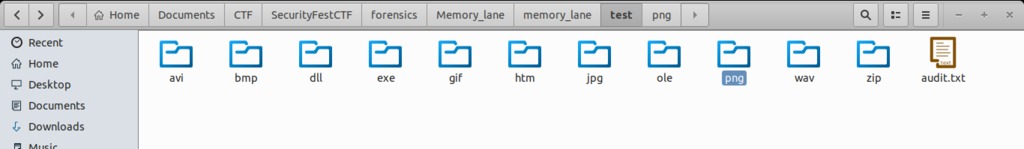
This questions belongs to forensics category so i have to search for flag in each and every folder. I go through all of the folder and in one folder name png which contains a lot of png images. I found qr code png image their.

I immediately scan it and boom i got the flag.
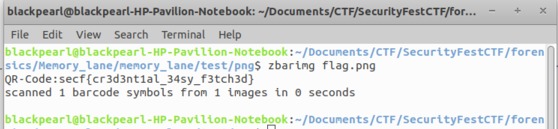
Flag:secf{cr3d3nt1al_34sy_f3tch3d} 