I enjoyed playing this ctf with my teammate. Here are the writeups of some challenges.
Web
Cryptography
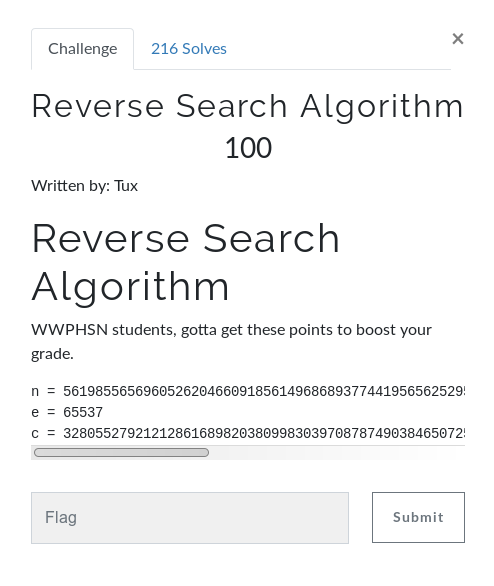
Reverse Search Algorithm
Massive RSA
Really Secure Algorithm
Welcome to Crypto Land
Forensics
Miscellaneous
Locked Up
A Simple Conversation
The Real Reversal
Hidden Flag
Broken REPL
Agent Keith
According to challenge name Agent refer to User agent of browser. The site look likes
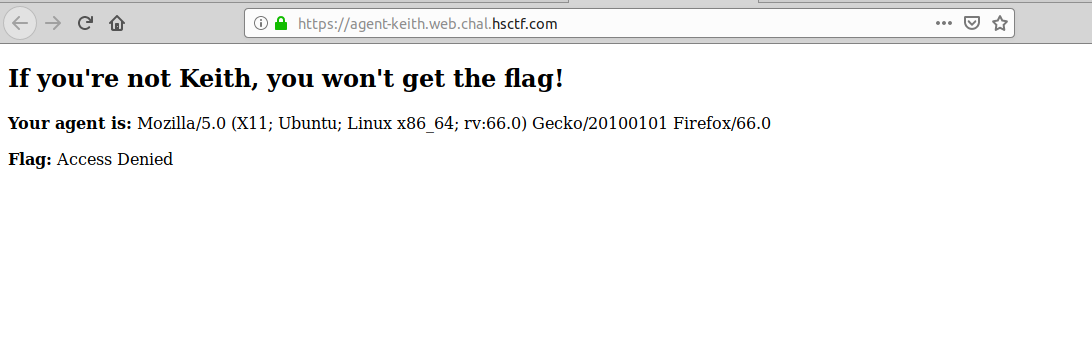
It shows the current user agent and flag as access denied. I go through the source code of website and found a removed user agent written their.
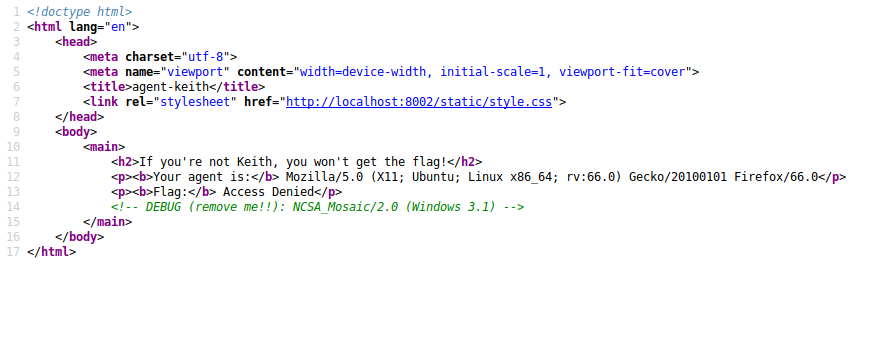
So i update the user agent to NCSA_Mosaic/2.0 (Windows 3.1) and in subsequect request i got the flag.
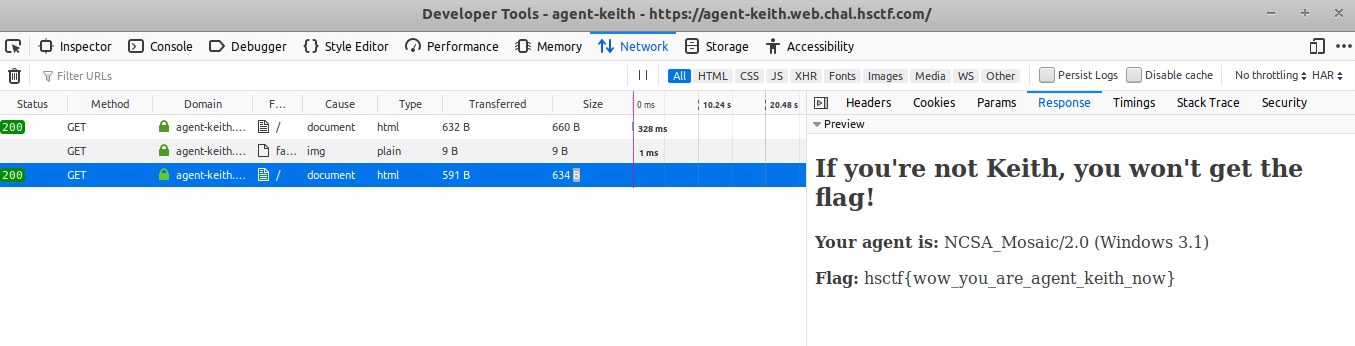
Flag:hsctf{wow_you_are_agent_keith_now} Reverse Search Algorithm
This challenge is on classic RSA encryption. I used Ganapati RsaCtfTool (Awesome RSA tool must check)to solve this challenge. Simply run this tool using given value of n,e and c where ‘n’ is public key ‘e’ is exponent and ‘c’ is cipher text.
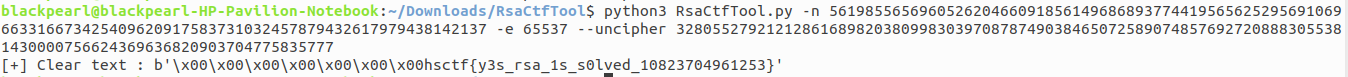
Flag:hsctf{y3s_rsa_1s_s0lved_10823704961253} Massive RSA
We have given a file massive.txt which contains valuse of n,e and c. This challenge is again on RSA encryption but with large value of n and c. I used Ganapati RsaCtfTool](https://github.com/Ganapati/RsaCtfTool) (Awesome RSA tool must check)to solve this challenge. Simply run this tool using given value of n,e and c where ‘n’ is public key ‘e’ is exponent and ‘c’ is cipher text. Simply run this tool using given value of n,e and c.
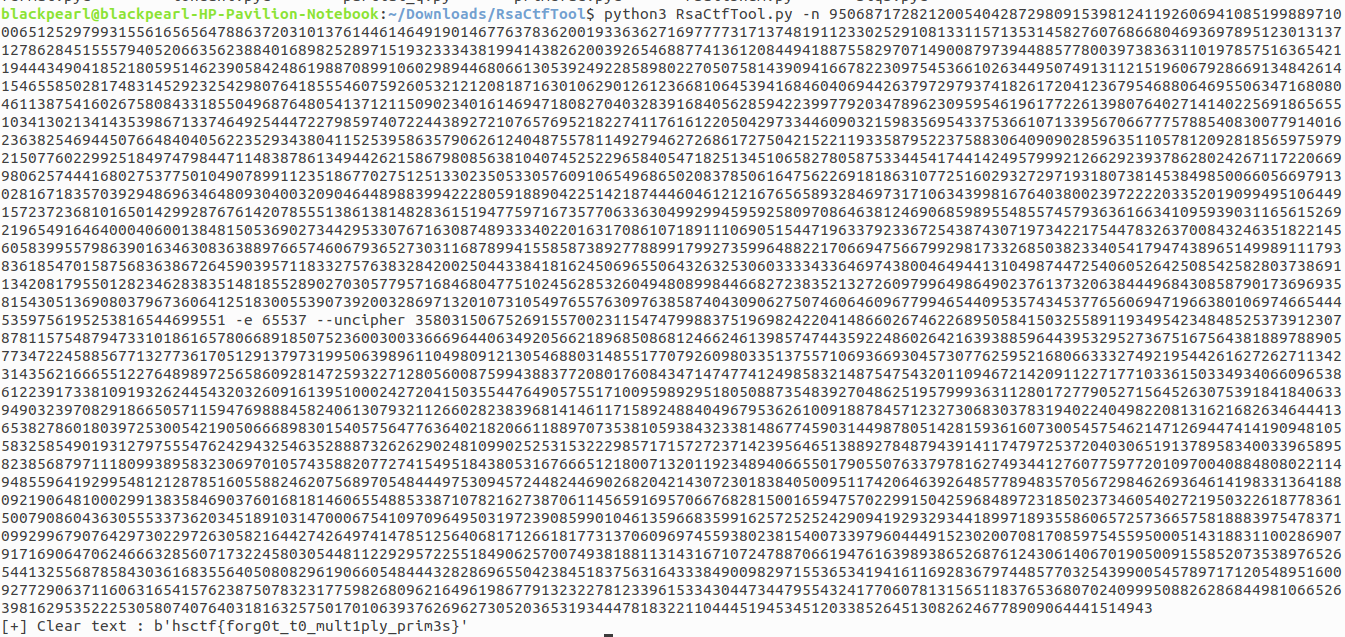
Flag:hsctf{forg0t_t0_mult1ply_prim3s} Really Secure Algorithm
We have give a file secure.txt which contains values of n,e and c where ‘n’ is public key ‘e’ is exponent and ‘c’ is cipher text. This challenge is again on RSA encryption. First we have to break value of n in to its prime factor so, i used online site factordb to find value of prime factor. We got only one value which is probably prime. Generally in RSA n break in to two prime factor.
p=16225510719965861964299051658340559066224635411075742500953901749924501886090804067406052688894869028683583501052917637552385089084807531319036985272636554557876754514524927502408114799014949174520357440885167280739363628642463479075654764698947461583766215118582826142179234382923872619079721726020446020581078274482268162477580369246821166693123724514271177264591824616458410293414647 So here we use phi=p*(p-1) instead of phi=(p-1)*(q-1) . To decrypt cipher we need to find private key ‘d’. Using value of phi and e we calculate modular inverse which is private key ‘d’. After that using private key ‘d’ , cipher text ‘c’ and public key ‘n’ we compute plain(numeric) message ‘m’ m=cd (mod n) by coverting m in to readable string we got the flag. I write a python program to solve this challenge. Python program here solve.py.
Flag:hsctf{square_number_time} Welcome to Crypto Land
In this challenge,a cipher text is given to decrypt.
cipher text: KZ6UaztNnau6z39oMHUu8UTvdmq1bhob3CcEFdWXRfxJqdUAiNep4pkvkAZUSn9CvEvPNT5r2zt6JPg9bVBPYuTW4xr8v2PuPxVuCT6MLJWDJp84 Given cipher is base58 cipher. I used online tool CyberChef to decrypt it.
Flag:hsctf{w0w_th1s_1s_my_f1rst_crypt0_chall3ng3?} Double Trouble
In this challenge two images are given koala.png and koala2.png. I try stings on both the png file but obtain nothing. I also search flag in metadata of png file but flag is not their. After a while i used zsteg to read lsb of png file and from koala.png i got a firebase link from where i downlaod a file hmmm.txt and lsb of koala2.png contain a passkey.
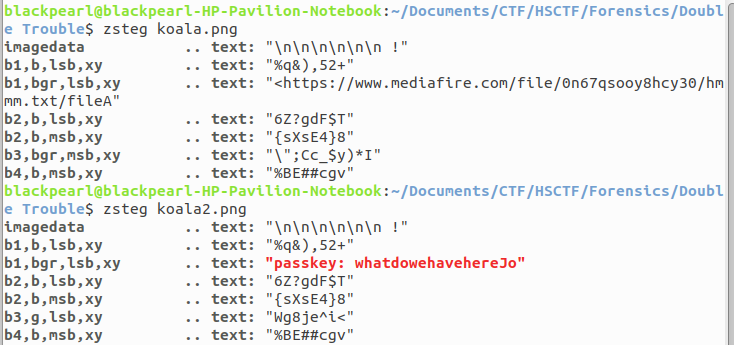
After checking file command on hmmm.txt i found that hmmm.txt is encrypted GPG symmetrically using AES cipher. I read about encryption and decryption of GPG symmetrically encrypted data. I decrypt hmmm.txt using gpg tool.
$ gpg --output flag.txt --decrypt hmmm.txt Running the above command it asks for password, by using passkey(16 bit from passkey) we have, it gives flag for this challenge.
Flag:hsctf{koalasarethecutestaren'tthey?} Locked Up
A zip file locked.zip is provided in this challenege. I first try to crack the password of zip file but it’s not successful. I see the content of zip file and i analyse that the zip file contains so many empty files, after that i think that the flag may be is in name of file so, i suddenly do strings on file and got flag for this challenge.
$ strings locked.zip | grep hsctf Flag:hsctf{w0w_z1ps_ar3nt_th@t_secUr3} A Simple Conversation
A service running at nc in which gives python shell and ask for input. I think that why not read flag directly in python shell so, by giving input as open('flag.txt','r').readlines() return the flag for this challenge.
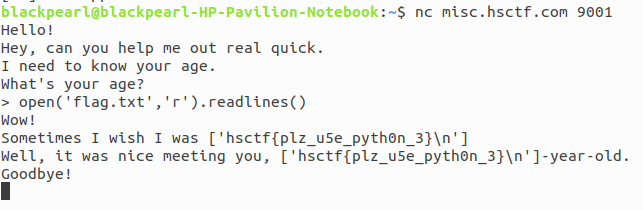
Flag:hsctf{plz_u5e_pyth0n_3} The Real Reversal
This challenge contains a file reversed.txt which contains the reversed of a original file means first the content of orinigal file is reversed then the byte of file is reversed. I write a simple python script solve.py which reverse the byte of file and the contents of file results in flag for this challenge.
Flag:𝚑𝚜𝚌𝚝𝚏{𝚞𝚝𝚏𝟾_𝚏𝚘𝚛_𝚝𝚑𝚎_𝚠𝚒𝚗} Hidden Flag
We have given a chall.png image file which is broken. I do strings and got a key as invisible. I solved this type of challenge in previous ctf so, immediately i write a python script which takes each byte of given file and do xor operation on each bytes, dumping the xor result gives us a png image which contains flag for this challenge.

Flag:hsctf{n0t_1nv1s1bl3_an5m0r3?-39547632} Broken REPL
A python file repl.py is given which contains the python program of running nc service. After reading the python program carefully, i found that if i raise MemoryError exception in python shell then i may get the flag. I googled a lot to raise exception in python shell, after trying some string to raise exception one string successfully raise the exception and gives flag for this challenge.
String:x=[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[[]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]] 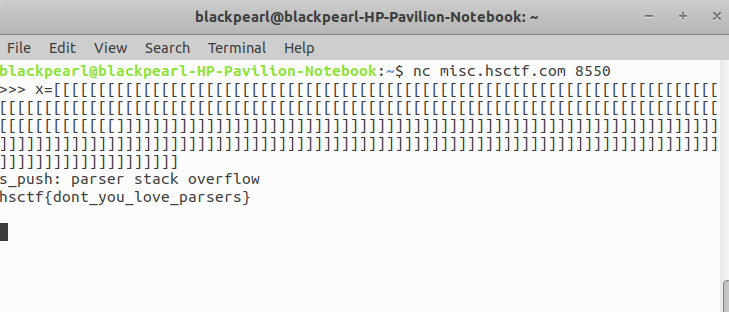
Flag:hsctf{dont_you_love_parsers}