EncryptCTF 2019 Some Challenges Writeups
Forensics
Steganography
It’s a WrEP
In this question, sniffed packet of wep network is given and we have to find the key of encryptCTF wifi network. I immediately think that wep is insecure and if we can analyse the sniffed pcap file using aircrack-ng tool(One of the awesome tool for network) then we will get the password of encryptCTF wifi network.
I run
aircrack-ng encryptCTFWEP.cap command in my terminal.
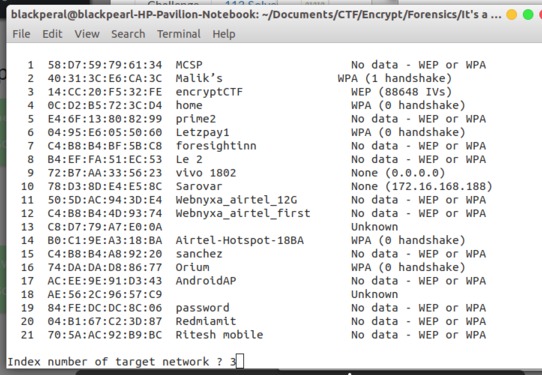
It asks for network index from given network in that file. Now index 3 is for encryptCTF wifi.
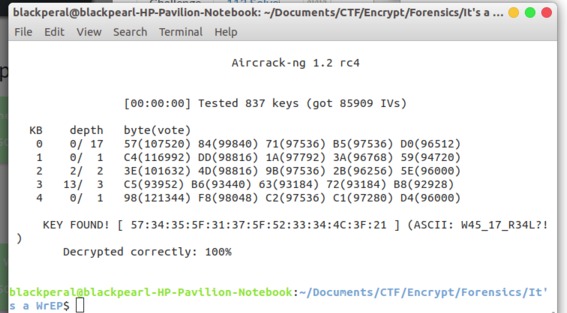
Type 3 and press enter you see the password(
W45_17_R34L?!).
Flag:encryptCTF{W45_17_R34L?!} Wi Will H4CK YOU
This question is similar than It’s a WrEP question but file contain WPA network sniffed packet. Again we have to analyse the give pcap file with aircrack-ng tool but this time we have to use wordlist to bruteforce the password.
Run
aircrack-ng encryptCTFWPA.cap -w rockyou.txt command (rockyou.txt is worldlist) in your terminal.
Again asking for network index this time type 1 and it takes some time to bruteforce the password and finally you left with
ThanckYou which is the password.
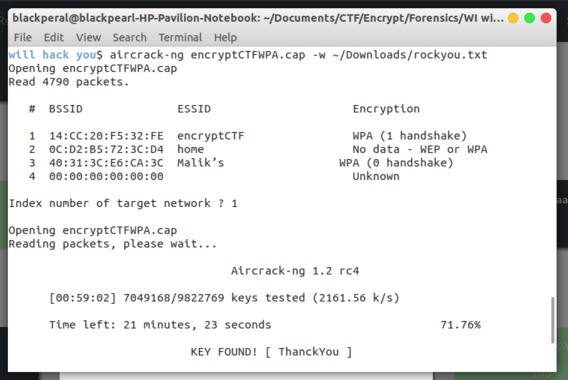
Flag: encryptCTF{ThanckYou} Into The Black
We have a image file.

It’s a one of the easy question. Simply use
Stegsolve tool to see other plane of given image. In Red plane 1 flag is written.
Flag:encryptCTF{L1GH7_17_UP} yhpargonagets
We have given a image file with jpg extension but when you see the type of file using file command in linux, you found that given file is a png image.
You change the extension of image but you can’t find anything there.
Challenge name is a hint, reverse the name of challenge. Steganography is a pip. You have to install steganography pip in your machine.
After that simply run
steganography -d encoded.jpg (-d to decode the image) command in your terminal which decode the image file into the flag for this challenge.
Flag: encryptCTF{pip_in5t411_5teg4n0graphy} 